
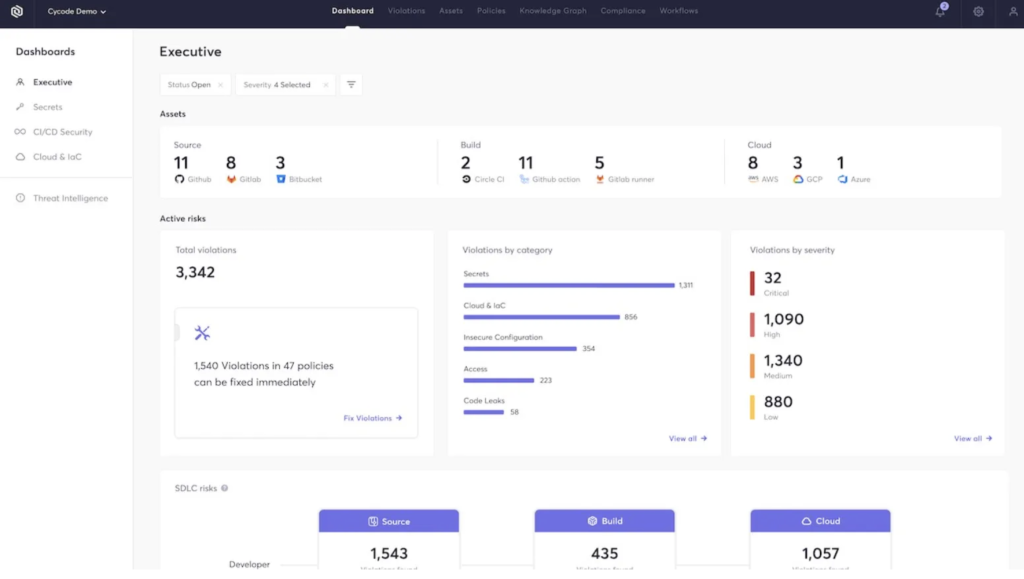
🔍 Introduction
As modern software development accelerates with DevOps and GitOps, security must be baked into every phase of the SDLC. Enter Cycode — a full-stack software supply chain security platform that unifies visibility and control across source code, pipelines, IaC, secrets, and more.
Cycode doesn’t just scan code; it integrates security across your entire development ecosystem. Think SAST, DAST, IAST, SCA, IaC, and CI/CD — all unified under one centralized policy engine.
🛡️ Core Features of Cycode
1. Source Control & CI/CD Security
- Detects hardcoded secrets, misconfigurations, and shadow repositories
- Supports GitHub, GitLab, Bitbucket, Azure Repos
- Prevents unauthorized access, detects branch protection bypasses
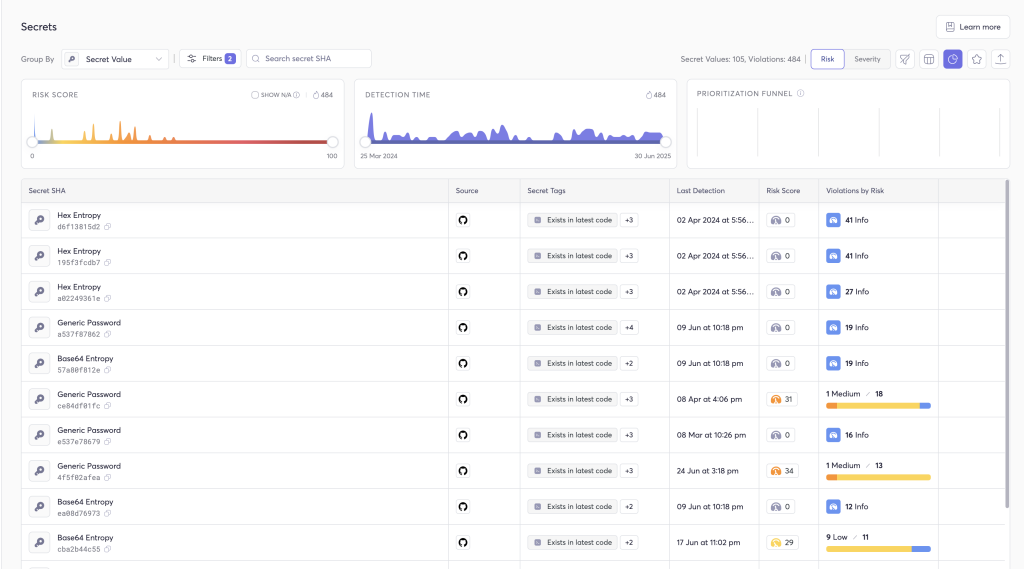
2. Secrets Detection & Management
- Real-time secret scanning across code, CI pipelines, containers
- Integrates with Vault, AWS Secrets Manager, and more
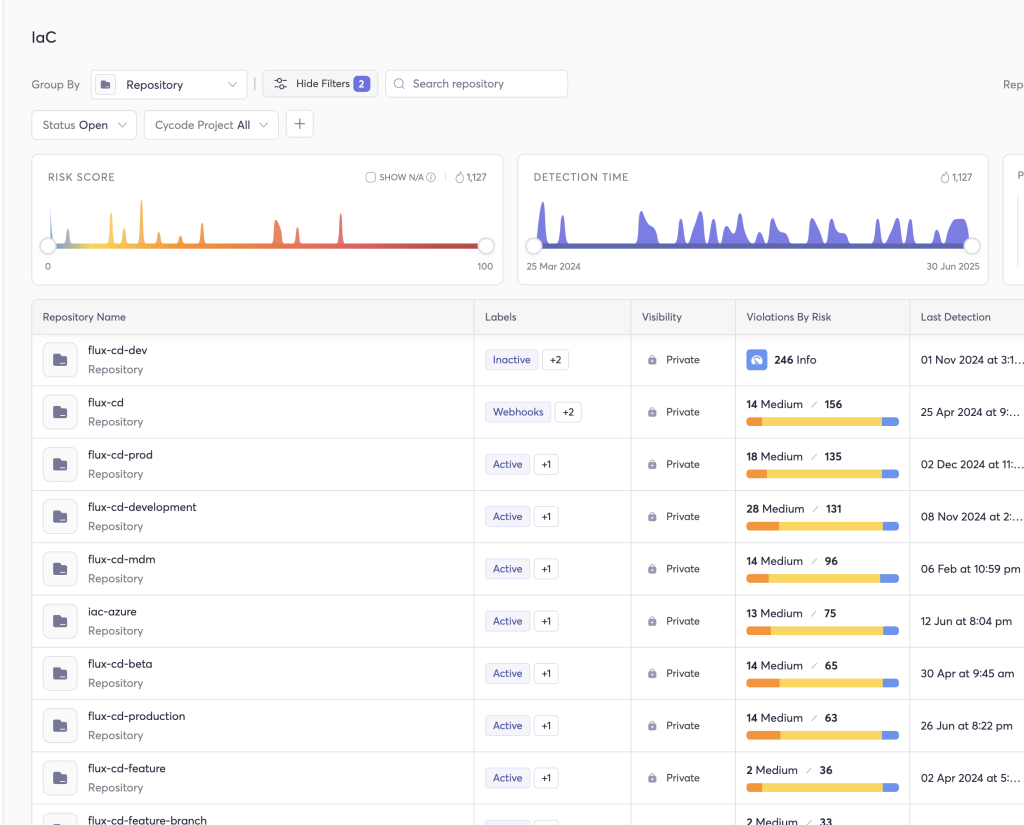
3. Infrastructure-as-Code (IaC) Security
- Static scanning of Terraform, CloudFormation, Kubernetes YAML
- Policy-as-code via OPA/Rego
4. Pipeline Integrity & Drift Detection
- Monitors CI/CD pipeline configurations
- Detects unauthorized changes, rogue script injections
5. SAST/DAST/IAST Integration
- Normalized aggregation of results from tools like Checkmarx, Veracode
- Centralized risk scoring with contextual intelligence
6. SBOM & Dependency Scanning
- Automated Software Bill of Materials
- CVE tracking, OSS license compliance
7. Policy Management Engine
- Define, enforce, and manage policies across the SDLC
- Supports GitOps and approval workflows
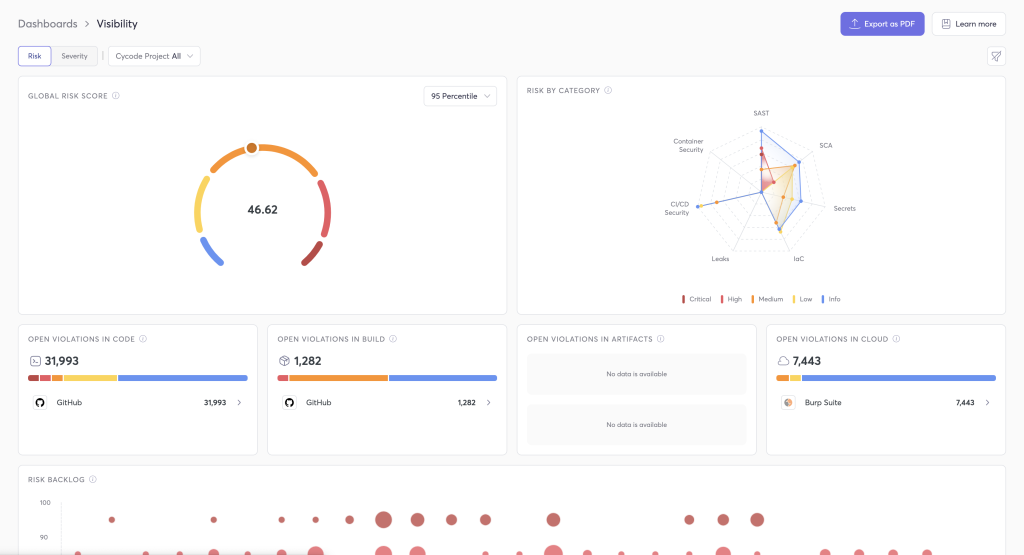
🧠 How Cycode Works
Cycode integrates via API hooks, CLI tools, SCM connectors, and webhooks. Here’s the high-level flow:
- SCM Integration: Connect GitHub/GitLab → scan repos for secrets, IaC, and misconfigurations
- CI/CD Integration: Monitor Jenkins, GitHub Actions, CircleCI pipelines for tampering
- IaC Scanning: Analyze Terraform, Kubernetes YAMLs pre-deployment
- Secrets Detection: Scan code, commits, containers, and environment variables
- Policy Engine: Automate enforcement with rules like “fail build if secret detected”
- Central Dashboard: View security posture, compliance mapping, and insights
⚙️ How to Integrate Cycode
1. Connect Source Control
- Go to
Integrations → Source Control - Choose your SCM (GitHub, GitLab, etc.) and authorize via OAuth
- Select repos to monitor and scan
2. Integrate CI/CD Pipelines
- Go to
Integrations → CI/CD - Select Jenkins, GitHub Actions, or other tools
- Example GitHub Action:
- name: Run Cycode Scan
run: |
curl -sSL https://cycode.com/install.sh | sh
cycode scan --repo .
3. Enable Secrets Detection
- Go to
Policies → Secrets Detection - Enable organization-wide scanning
- Integrate with HashiCorp Vault or AWS Secrets Manager
4. Scan IaC Configurations
- Enable scanning of
.tf,.yaml,.jsonfiles via PR hook - Violations are auto-commented in the pull request
5. Configure Policy Management
- Define rules like:\n — “Block merge if AWS secret key detected”\n — “Alert if unencrypted S3 bucket is provisioned”\n- Supports OPA/Rego policy definitions
6. Alerting & Notifications
- Go to
Settings → Notifications - Connect Slack, Teams, Jira, SIEM tools for alerts
🔐 Real-World Use Cases
- Enforce GitOps policy compliance via PR checks
- Detect secrets in real-time across your repos
- Get visibility into rogue pipeline executions
- Auto-generate SBOMs and track vulnerable dependencies
✅ Key Benefits
- Unified Platform: Reduce tool sprawl with one platform
- Developer-Centric: Inline PR feedback and CLI support
- Policy-as-Code: Enforce rules directly in Git
- Compliance Ready: Map to NIST, ISO, SOC2
- High Fidelity Alerts: Context-rich, noise-free
🔚 Final Thoughts
Modern delivery pipelines require modern security. Cycode empowers engineering and security teams with an integrated, context-aware, and automated solution to secure the entire SDLC.
From commit to cloud, Cycode has your back.

